Note: this article applies to Linux users. For Windows users, check out Sandboxie.
This is a gentle introduction to Firejail, a sandboxing tool for Linux.
Introduction
Firejail is a powerful sandboxing tool for Linux that enhances the security of running applications by isolating them from the rest of the system and restricting their access to resources (in particular: file system, network).
As described by the authors:
Firejail is a SUID sandbox program that reduces the risk of security breaches by restricting the running environment of untrusted applications using Linux namespaces, seccomp-bpf and Linux capabilities. It allows a process and all its descendants to have their own private view of the globally shared kernel resources, such as the network stack, process table, mount table. Firejail can work in a SELinux or AppArmor environment, and it is integrated with Linux Control Groups.
A GUI application for use with Firejail is also available, firetools.
You may already be familiar with namespaces and other containerization techniques, so this tool is an excellent way to leverage the capabilities of your Linux system.
Installation
Simply install the firejail package from your distro.
Usage
Firejail is bundled with hundreds of ready to use profiles for common applications. This includes popular software like VLC but profiles are (surprisingly) even available for more specialized applications such as ZAP (zaproxy), a penetration testing tool for testing web applications.
To execute an application using firejail’s default profile you can run following command:
firejail <program_name>
Using Firejail by default
To use Firejail by default for all applications for which it has predefined profiles, run the firecfg tool with sudo:
sudo firecfg
This creates symbolic links in /usr/local/bin/ pointing to /usr/bin/firejail for programs for which Firejail has default or self-created profiles. Note that firecfg only symlinks the programs listed in /etc/firejail/firecfg.config.
Profiles are usually found in /etc/firejail. For example the relevant entry for VLC is located at /etc/firejail/vlc.profile.
Creating profiles for your applications
You can either generate a new profile like this:
firejail --build application
Or use an existing, suitable profile as a template.
For a more granular approach, you can start with the template available at: /usr/share/doc/firejail/profile.template. Then gradually comment/uncomment the various options while checking at each stage that the application runs properly inside the new sandbox. Do not change the order of the sections in that template.
See the docs for details.
Customizing profiles
As mentioned in the .profile files:
This file is overwritten after every install/update
Therefore it is recommended to create override files instead. They can either reside in /etc/firejail/ or in ~/.config/firejail/.
See the doc: Persistent local customisation
Verifying Firejail is being used
To list the loaded applications currently using Firejail run this:
firejail --list
Example:
342220:user::/usr/bin/firejail /usr/bin/vlc --started-from-file
Example commands
Running bash with only one network interface visible
firejail --noprofile --net=enp5s0 bash
Then:
ip a
Output:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host proto kernel_lo
valid_lft forever preferred_lft forever
2: eth0-340785@if3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 9e:fa:02:13:c9:35 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 192.168.0.40/24 brd 192.168.0.255 scope global eth0-340785
valid_lft forever preferred_lft forever
inet6 2a01:6f01:1205:ca00:9cfa:2ff:fe13:c935/64 scope global dynamic mngtmpaddr proto kernel_ra
valid_lft 172793sec preferred_lft 86393sec
inet6 fe80::9cfa:2ff:fe13:c935/64 scope link proto kernel_ll
valid_lft forever preferred_lft forever
As you can see that the interface appears as eth0-340785@if3 in this context. It has got its own IP stack with IPv4 and IPv6 addresses, and the MAC address is also different than the physical MAC address.
Running bash with no network access
firejail --noprofile --net=none bash
Only the loopback interface will be visible in this configuration.
Private mode
Firejail also includes a one time private mode, in which no mounts are made in the chroots to your home directory. In doing this, you can execute applications without performing any changes to disk.
Example:
firejail --seccomp --private bash
You can also use an existing directory as home for your sandbox. This allows you to have a persistent home for your application:
Debugging and troubleshooting
Firejail can cause subtle issues or make program misbehave in a way that is not always immediately obvious. If you suspect issues with Firejail, try running the offending application bypassing Firejail or by using the –noprofile command option.
Most issues usually boil down to file system issues (lacking permissions or files missing in scope of sandbox).
The most straightforward way to debug Firejail is to run the application from the command line and look at console output for possible error messages. The application may also keep its own logs.
For example, running vlc from the command line would show this line:
Reading profile /etc/firejail/vlc.profile
This confirms the location of the profile file being used.
Or just use:
firejail --debug <program_name>
Case study: troubleshooting VLC
Problem description: when running VLC through Firejail, the vlsub extension does not appear. Vlsub is an extension written in Lua, that is used to fetch subtitles.
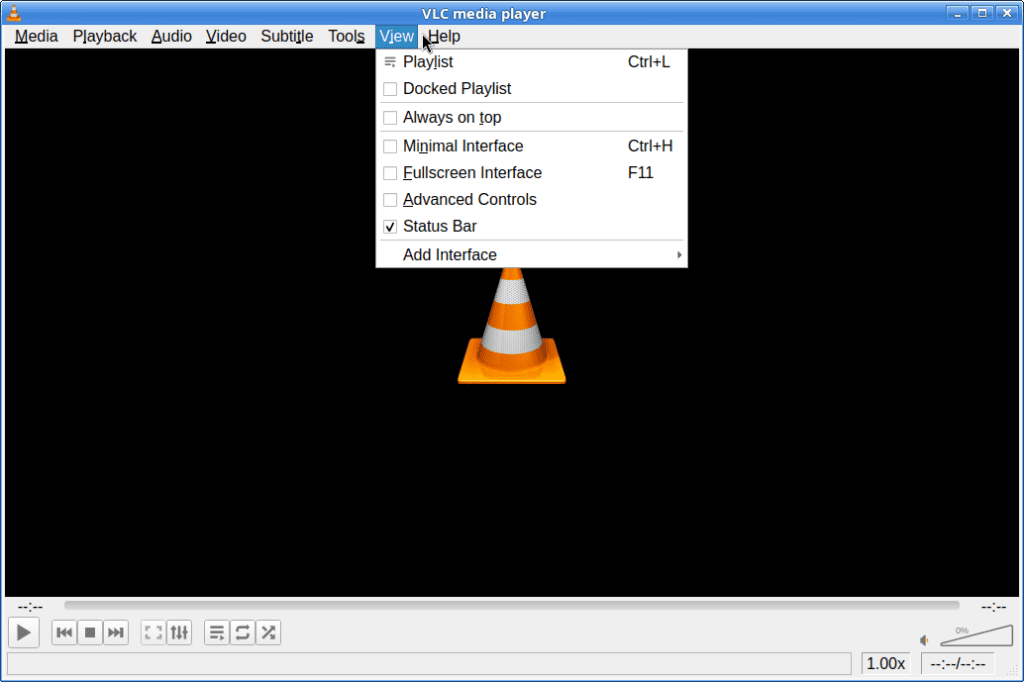
vlsub extension missing
Running vlc with option –verbose 2 gives some clues as we can see the following lines in console:
[0000750ee416b3d0] main generic warning: cannot load module `/usr/lib/vlc/plugins/lua/liblua_plugin.so' (liblua.so.5.4: cannot open shared object file: Permission denied) [0000750ee416b3d0] main generic debug: no extension modules matched [00005c08dfc0b820] qt interface error: Unable to load extensions module
If we examine file /etc/firejail/vlc.profile we can spot this line:
include disable-interpreters.inc
And indeed the loaded profile disables the Lua interpreter, which is causing our issue. If we look inside that file (/etc/firejail/disable-interpreters.inc) we can see the following:
# Lua
blacklist ${PATH}/lua*
blacklist /usr/include/lua*
blacklist /usr/lib/liblua*
blacklist /usr/lib/lua
blacklist /usr/lib64/liblua*
blacklist /usr/lib64/lua
blacklist /usr/share/lua*
We can simply re-enable Lua by adding an override file in ~/.config/firejail/lua.local with a line like this:
include allow-lua.inc
VLC should now be able to load the vlsub extension:
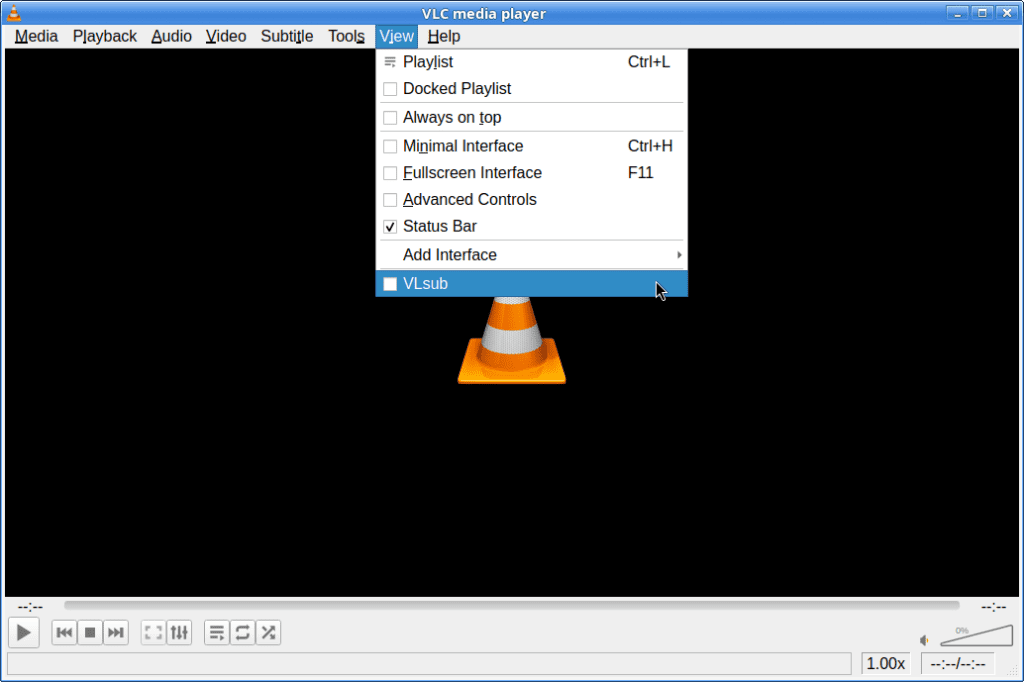
vlsub extension is now loaded
Case study: Libre Office: keyboard not responding
This issue can happen when using ibus. Running Libre Office with the –nodbus fixes the issue:
firejail --nodbus soffice
To fix this issue we can create an override file in ~/.config/firejail/soffice.local and add these two lines:
dbus-system none dbus-user none
NB: the ~/.config/firejail/ directory may not exist yet, then create it.
Source: https://forum.manjaro.org/t/no-keyboard-input-when-using-firejail-after-31-03-2023-update/137576
Conclusion
Firejail is a flexible yet poweful tool that can be used almost straight out of the box to increase your personal security posture in a significant way. You can use it to restrict access to private files, or deny applications the ability to communicate with the rest of your network – or the Internet. More advanced use cases like traffic shaping are also possible.
Firejail can be run on demand for specific programs, which is recommended when trying out untrusted software.
Due to the inevitable and sometimes arcane issues that can arise with such a tool, it may not be suitable for beginner Linux users.
References
- Firejail home page
- Firejail wiki (Arch Linux)
- How to debug a firejail sandbox
- Firefox Sandboxing Guide